In a statement, Twitter said that it had “detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools. We know they used this access to take control of many highly-visible (including verified) accounts and tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.” Twitter said that it first became aware of the incident late afternoon Pacific Standard Time. It moved to remove the tweets and disable the affected accounts. Likewise, as a precautionary measure, it also temporarily disabled the ability for verified twitter accounts — with a blue checkmark — to tweet. “This was disruptive, but it was an important step to reduce risk. Most functionality has been restored but we may take further actions and will update you if we do,” Twitter wrote. The company said it is now looking into any other “malicious activity” the attackers may have conducted. Online security experts speculated that if attackers were able to compromise Twitter accounts in such a form, they might also have access to the direct messages those accounts had received.Tough day for us at Twitter. We all feel terrible this happened.
We’re diagnosing and will share everything we can when we have a more complete understanding of exactly what happened. 💙 to our teammates working hard to make this right. — jack (@jack) July 16, 2020
What is social engineering?
In the context of cyber security, “social engineering” is the act of tricking employees, rather than brute hacking of code, to gain access to buildings, systems or data. Often it involves impersonating another person, such as a senior-level executive at a company. In the crypto community, a popular social engineering attack is SIM-swapping. In this case, the attacker impersonates the target and asks a customer service representative at a telecom for a new SIM card, allowing the attacker to receive second-factor authentication texts sent to the target’s phone number.Was the Twitter hack an inside job?
The social engineering explanation is seemingly at odds with other theories of how the hack was executed. According to a report from Motherboard, which cited sources supposedly involved in the attack, a Twitter insider was paid to compromise the social platform. “We used a rep that literally done all the work for us,” Motherboard quoted a source as saying. Motherboard showed screenshots from the purported hackers that supposedly show the “God mode” tool used to provide root access. The screenshots depict numerous high-profile Twitter accounts being manipulated, including that of Binance.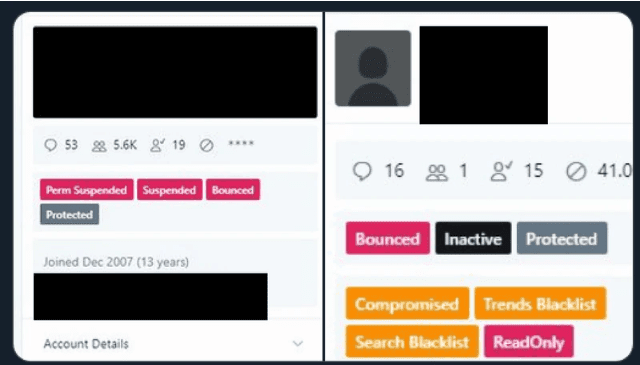
A tool that was reportedly used to manipulate accounts (source: Motherboard)
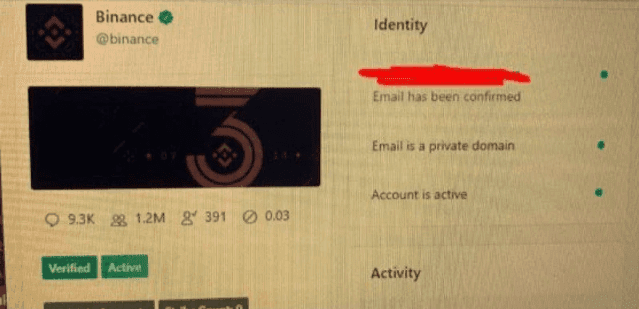
Another screenshot of the tool used by a Twitter insider to manipulate the account (source: Motherboard)