The bitcoin halving is expected to happen on Tuesday, May 12, as the 210,000th block gets mined and bitcoin miner’s reward will be reduced from 12.5 BTC to 6.25 BTC.
The world’s first and still most popular cryptocurrency has taken the market for a roller coaster ride for weeks up to now, with its extreme price volatility on full display.
Just over this weekend, the so-called “digital gold” took a 15% nose dive in less than an hour. But this tumble followed a week of a historic bull run on bitcoin that included a $35 billion increase in market volume in just 24 hours.
Bitcoin uses a consensus mechanism called “proof of work” (PoW) as a method for miners (nodes) to verify the information and form new blocks on a blockchain, in order to earn new bitcoin. This so-called “miner’s reward” gets reduced to half after every 210,000 blocks mined, which takes place roughly every four years. The next “bitcoin halving” event is expected to happen sometime in the next 24 hours. So, starting less than a day from now, bitcoin miners everywhere will be forced to work a lot harder to “prove their work” to earn the same amount of bitcoin as before.
To fully understand just how much miners sweat for their coins, let’s now take a closer look at how Bitcoin relies on proof of work to verify transactions, remove third parties and incentivize nodes.
An idea that begat Bitcoin
Proof of work was the first and still the most common consensus mechanism used in cryptocurrencies. It is the DNA of bitcoin as well as the earliest blockchain, and it is represented by a 32-bit data that is used to validate the information stored within a block. This 32-bit data, often called “nonce” (number only used once), is expensive and time-consuming to generate but easy to verify.
The concept was first introduced in a paper written in 1993 by its inventors, computer science professors Cynthia Dwork of Harvard University and Moni Naor of Weizmann Institute for Science in Israel. Although it was initially designed as a mechanism to battle spam and distributed denial of service (DDoS) attacks, PoW’s most famous and popular use to date is Bitcoin.
How are transactions verified?
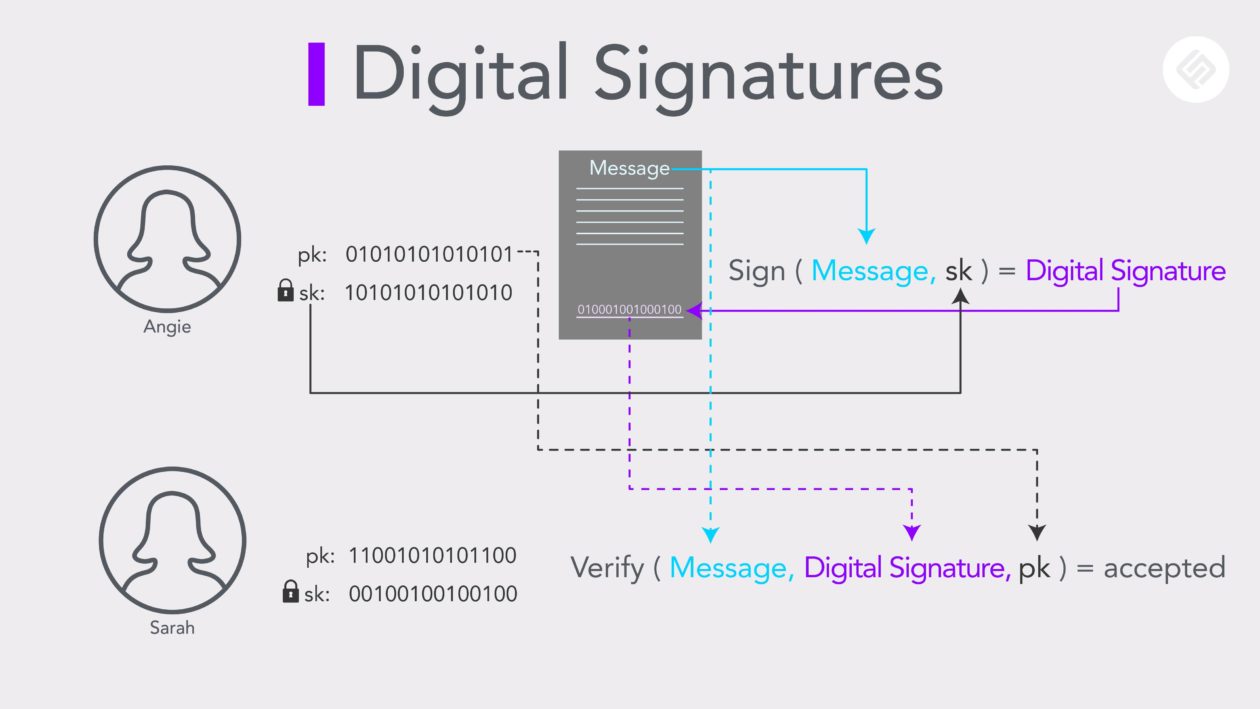
In a cryptocurrency network, each participant has a set of keys: a private key (sk), and a public key (pk) that are used to produce and verify a digital signature. This signature is used by participants to confirm their involvement in transactions.
Unlike our handwritten signatures, digital signatures vary for every instance and are represented by hash. The expected signature is dictated by the information that composes a transaction. (So no need to worry about someone else forging or duplicating your digital signature!)
A digital signature is produced using your private key that only you, the owner, have access to. The public key can be used by others to confirm the digital signature is indeed one that has been produced by the private key associated with your public key.
Removal of third-parties
Now that PoW’s verification system has eliminated the threat of forgery, another concern arises: “How can we trust every participant to broadcast valid information?” In traditional information systems or centralized databases, an independent third entity manages this ledger. But in blockchain, this is where proof of work comes in.
When a hash function is applied to the message that is signed with the digital signature, the final 256-bit hash is produced.
Now, to further influence this final hash, a number called nonce is added to the end of a transaction. The role of this number is to influence the final hash so that it will begin with a certain number of consecutive zeros.
As inverse computation is not possible in this form of cryptographic hash function, the only way to obtain this nonce is through trial and error.
But how difficult could it possibly be to figure out a number?
For the sake of this example, let’s say we’re trying to figure out the nonce that would dictate a final hash to begin with 30-zeros, and let’s also say that our hash is composed of just 1s and zeros, or two possibilities per bit.
This would bring our probability to ½30, or one in a billion chance to guess the number.
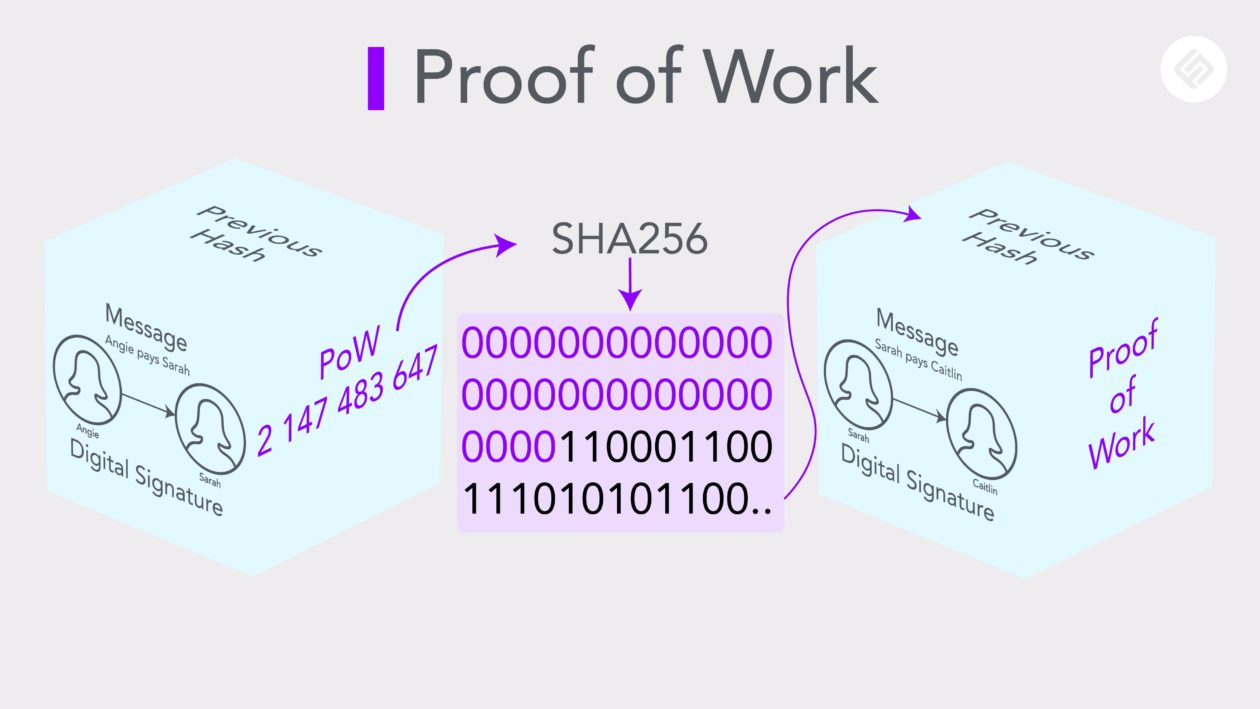
Figuring out the nonce, which would require extensive time and computational work, would prove that someone has done the work required to identify this number, hence “proof of work.”
Once the nonce has been identified, other participants can run SHA256 on this number to instantly confirm the validity of the nonce.
All this information is then compressed into a block and added to a chain. When a new block is formed, it also contains the hash of the previous block, which is also one of the factors that dictates the hash of the new block.
If a person with malevolent intent were to change the data stored within a blockchain, it would require more than 50% of the entire network’s computational power to continue producing nonces at a speed faster than the rest of the network.
Any equal to or less than 50% of the network’s computational power, the rest of the network will eventually question the bad actor’s lack of computational power and validity, and reject its attempt to alter data in a blockchain.
Incentivizing proof of work
This computational method of block creation consumes a lot of time and energy. So why would anyone do it?
The answer is what is called a miner’s reward.
For bitcoin, block creators who perform enough cryptographic work are rewarded with BTC, therefore adding a valued resource (in the form of cryptocurrency) into the economy — hence mining.
The Bitcoin protocol ensures that a block is mined, somewhere in the world, every 10 minutes on average. It does this by periodically changing the number of starting zeros in the final hash.
Technically, as more miners join the network, mining speed should improve over time. But by adjusting the number of zeros, the difficulty for guessing the PoW will adjust as well. Because there are no shortcuts and only raw computational power is required for mining, typically only miners with access to free or low-cost electricity for powering their mining machinery can “prove” enough to profit from their “work.”
Criticisms of proof of work
The biggest threat to a proof-of-work system is what is called the 51% attack. Because mining has become so competitive and expensive, many miners join mining pools or groups of miners. Together, they have a higher chance to guess the correct nonce and receive the miner’s reward in this lottery-like award distribution system. If some of these groups decide to join forces, they can potentially have more than 51% of the network’s computational power. In essence, if a group or actor is large and powerful enough, it can dictate what is true and what is false and take over.
In the real world, 51% attacks have occasionally occurred. January of 2019, Coinbase detected 15 reorganizations of the Ethereum Classic (ETC) blockchain, with 12 of these as double spends totalling more than 219,000 ETC, or about 1.1 million USD at the time. Luckily, Coinbase suspended all ETC trades after detecting the unusual activity and no Coinbase accounts were affected.
The so-called 51% attacks have also been used to defend against 51% attacks. In May last year, Bitcoin Cash mining pools BTC.com and BTC.top orchestrated a 51% attack on the network in order to reverse invalid transactions from an unknown miner.
But a sufficient defense isn’t always mounted in time. Earlier this year, malevolent miners hit Bitcoin Gold with two 51% attacks in two days and made off with $72,000 through double-spending. The successful heists came after a notorious 51% attack on Bitcoin Gold in 2018 that resulted in an $18 million loss.
Another criticism towards the PoW mechanism is its enormous power usage.
According to the Cambridge Centre for Alternative Finance, bitcoin mining consumes about 83 terawatt-hours (TWh) per year.
As of this publication date, if bitcoin were a country, it would rank 35th in annual electricity consumption in the world, more than all of Finland and just behind Pakistan.
The disadvantages of proof of work have brought about several alternative consensus mechanisms, such as the delegated proof of stake (DPOS) and the Federated Byzantine Agreement (FBA). Perhaps the most popular is proof of stake (PoS). By distributing validating power depending on how much stake a person has in a network, proof of stake improves some of the challenges faced by proof of work. But proof of stake comes with its own baggage and issues. To find out more about this alternative consensus mechanism, check out the Forkast explainer on proof of stake.
See related article: What is proof of stake?