The culprits behind the recent 51% attacks on Ethereum Classic used rented mining hash power to carry off their heists, exploiting a vulnerability common to cryptocurrencies that rely on “proof of work” as their underlying technology.
Rented mining hash power is at the center of all three attacks on ETC last month, which resulted in millions of dollars in losses and delivered a significant blow to the reputation of PoW protocols previously believed to be immutable and “unhackable.”
“It’s actually a huge vulnerability in the system,” said Terry Culver, CEO of ETC Labs, an incubator of projects on Ethereum Classic, in an interview with Forkast.News.
“Three attacks in one month will tell you that security is an issue on Ethereum Classic. And we believe and know that other blockchains get attacked more regularly, maybe with less visibility,” Culver said. “It’s a universal problem.”
The cryptocurrency space has been trying to weed out criminals and tighten up security, including the implementation of “know your customer” and anti-money laundering (KYC/AML) procedures, increased regulations from governments, and enhanced security systems to stave off hacking.
But despite these efforts, malicious actors continue to exploit a core feature of many blockchain systems — decentralization and the requirement that there must be a 51% consensus of the protocol’s nodes to control the network.
“The [cryptocurrency] system is maturing, but the hash rental market is actually growing,” Culver said. “Think of it like, you turn the light on, and where do the mice go? [Malicious actors have] left the exchanges for the most part, and they’ve moved into the hash rental market.”
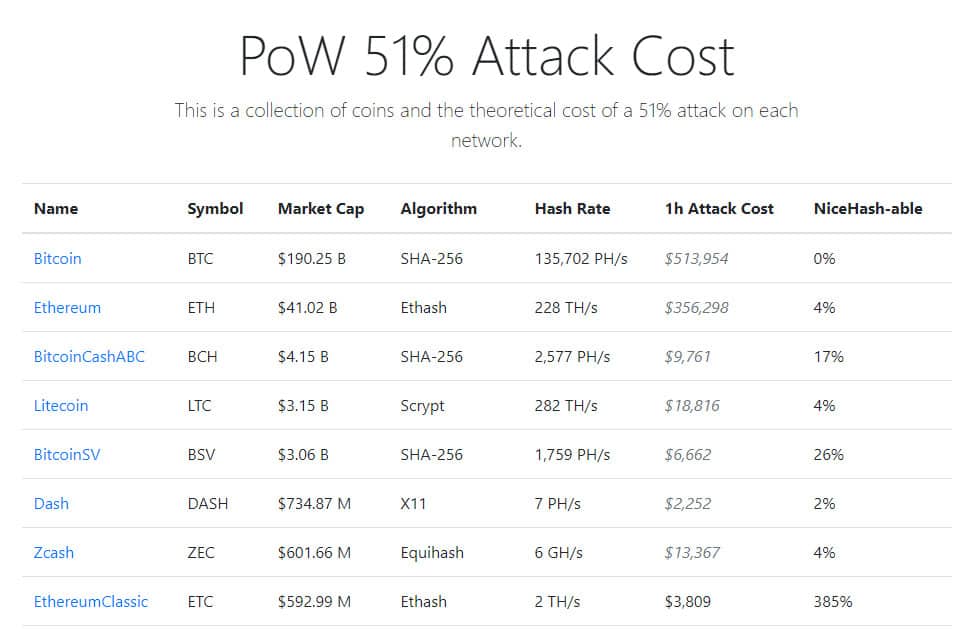
Proponents of PoW systems would say that the 51% requirement needed to gain consensus would make it very hard to hack large blockchain protocols like Bitcoin and Ethereum. But there is still a theoretical possibility if someone or a group manages to gain 51% control over those networks. The risks of a 51% attack increases for smaller cryptocurrencies that don’t have as many nodes, as it would be relatively easier to take over the network of a smaller network while still turning a profit.
For example, it would take over US$513,000 to perform a 51% attack (at the time of this publication) for one hour on Bitcoin, but only about US$3,800 for a similar attack on Ethereum Classic, which is why the smaller network may be much easier and more profitable for malicious actors to attack.
“The hash rental market is like under a rock somewhere, it’s totally anonymous,” Culver said. “They’re basically money laundering operations. So you could take your BTC from ill-gotten gains, rent hash power, and get out freshly-minted tokens with no provenance.”
What does renting hashpower do?
How did they do it? The malicious actors behind the first two attacks on ETC in August were able to achieve 51% dominance over the network by renting hash power from NiceHash provider daggerhashimoto, based on an analysis by Bitquery, a data intelligence firm.
Slovenia-based NiceHash is an online platform where customers can rent hashing power from sellers providing the computing power to mine cryptocurrencies.
By using this rented hash power, the attackers behind the first and second attacks on Ethereum Classic were able to “double spend” over US$7 million by overwriting entries in the blockchain, reversing or even changing the destination of transactions. In other words, the attackers had almost complete control over the network and were able to route money as they pleased.
NiceHash has previously been embroiled in controversy. In 2019, its former chief technology officer and co-founder Matjaz Skorjanec was arrested in Germany over U.S. charges of being involved in a hacking group that organized the theft of millions of dollars.
NiceHash itself was hacked in 2017, resulting in the loss of an estimated US$78 million in bitcoin.
The August hacks were not the first time Ethereum Classic suffered from such breaches, as a similar 51% attack occurred against ETC in January 2019. Hackers have also launched successful 51% attacks on a number of other smaller cryptocurrencies, including Bitcoin Gold, Verge and Monacoin in 2018.
“Computers are getting better, it’s going to keep getting easier and easier to get control of the computer power necessary to do these things,” said Benjamin J. A. Sauter, partner at New York-based international law firm Kobre & Kim, which is representing ETC Labs in investigating and suing the hackers.
Moreover, the concentration of hashing power in China has also been shown to be a risk for cryptocurrencies, as recent flooding in the country’s Sichuan province destroyed thousands of crypto miners. Sichuan province, which is known for its cheap hydropower, has been a popular location for cryptocurrency mining farms looking to save money, but the floods and landslides caused a distinct drop of BTC hashrate in Chinese mining pools.
See related article: How Ethereum Classic’s 51% attacks reveal risks to Bitcoin and Ethereum
In a statement addressing the recent attacks and allegations from ETC Labs, NiceHash says that it “does not support or enable 51% attacks” but also concedes that its hash power “might be abused by the attacker’s pool.”
NiceHash says it takes steps to prevent or help prevent market disruptions and manipulations, and cooperates with law enforcement conducting investigations on activities which break their terms of service and privacy policy.
Forkast.News has reached out to NiceHash for additional comment, but has not received a response as of the time of writing.
Self regulation vs government intervention?
Despite the hacks and the numerous monetary losses, the crypto community have largely said they prefer to pursue malicious actors privately instead of bringing in greater government regulation and scrutiny.
As a result of the attacks on Ethereum Classic, ETC Labs has announced that they are developing a strategic plan to protect the integrity of the ETC ecosystem. The plan includes cooperating with miners to maintain a consistent hash rate on the network, advanced monitoring to identify anomalies or spikes in the hashrate, and eventually changing the PoW mining algorithm.
“By and large, I think the space doesn’t want the government to become deeply involved in how the exchanges operate and try to remedy wrongs,” Sauter said. “I think the industry as a whole wants to be able to self-regulate and have an environment where the government doesn’t need to be in the weeds. But as long as there’s not an effective private resolution, it’s how problems are going to be solved.”
This is a thought-provoking observation. 🤔
— Charlie Lee [LTC⚡] (@SatoshiLite) January 8, 2019
By definition, a decentralized cryptocurrency must be susceptible to 51% attacks whether by hashrate, stake, and/or other permissionlessly-acquirable resources.
If a crypto can’t be 51% attacked, it is permissioned and centralized. https://t.co/LRCVj5F0O1
The cryptocurrency industry has seen increasing government interest, stricter rules and moves toward regulations in recent times, including the U.S.’ Financial Action Task Force’s guidelines for virtual asset service providers like exchanges to include the personal information of people transacting over US$1,000.
Another U.S. agency, the Commodity Futures Trading Commission (CFTC) also announced a strategic plan to regulate cryptocurrencies by 2024. The U.S. Security and Exchange Commission (SEC) may also be on track to shift its views on how it determines cryptocurrencies to be securities, according to SEC commissioner Hester Peirce.
“Capital markets can transform people’s lives, and so allowing the financial system to reach more people means that we have to really revisit some regulatory features that are in place now,” Peirce said in an interview with Forkast.News. “Crypto is an opportunity for us to be introspective and to say, hey, are we handling innovation right?”
Rented hash power might be a new sector where the industry may prefer to resolve disputes privately before the government steps in, Sauter said.
“If you don’t [have a framework for private dispute resolution], the only other choice that the victims of frauds have is to go to the government,” Sauter said, adding that those actions led to a wide crackdown on cryptocurrency business by the SEC and CFTC. “The industry would like for the government to take a hands-off approach, but that’s just not going to be a long-term, feasible solution if there’s also no way to figure out who is abusing the system.”
To bring the cryptocurrency industry out of the Wild West of scams and hacks that proliferated during the ICO bubble of 2017 would require increasing controls and checks on the system — through government or private organizations.
“If there’s a market for renting, I don’t think that itself is a problem,” Sauter said. “But if you’re doing it without keeping track of who your customers are and doing the same kind of due diligence that the exchanges are doing now, so that you’re able to trace back these kinds of frauds and hold people accountable when they abuse it, then you’re part of the problem, not the solution.”
NiceHash begs to differ.
“Just like ISPs can’t guarantee that all internet traffic is not malicious, NiceHash cannot be responsible for the security of every blockchain infrastructure,” the hash power provider said, in a statement. “The question of security becomes the question of the community and its creators. We must accept that if we want a true decentralization.”